The (Cyber) Storm is Coming. Are Your Clients Protected?
Submitted by Denyse Cromwell-Mackey on

IT security, a.k.a. cyber security, is the pressing topic on everyone’s mind — from the board of directors to the IT tech. Every day headlines scream about sophisticated new attacks on major websites, media, and tech companies and new data breaches. If you search the web for IT security, Google returns a mind-blowing 392 million results.
Record-Breaking Year
The odds are that you have received at least one notification that your credit card or personal data has been compromised, if not more than one. According to the annual IBM Security Services 2014 Cyber Security Intelligence Index, 2013 was a record-breaking year with more than half a billion records of personally identifiable information — including names, emails, credit card numbers, and passwords — stolen.
IT security issues continue to be one of business’s major challenges. IBM’s global monitoring operations and analysts have determined that the average company experienced more than 91 million security events in 2013 — a 12 percent increase over 2012.
Over 75 percent of incidents target the same five industries, and the top two industries, finance/insurance and manufacturing, account for nearly 50 percent of security incidents in 2013, as shown in the graph below.
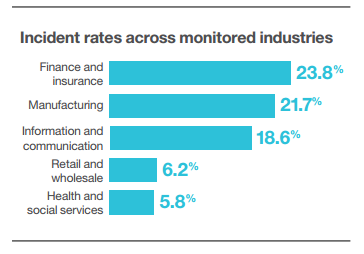
Not surprisingly, the top two industries are the ones that offer attackers significant potential payoff. It’s easy to imagine how accessing financial data or blocking online banking services could result in massive cash losses and major business disruption. And it’s chilling to think about what attackers could gain by uncovering proprietary manufacturing processes or product formulas.
Staggering Costs
The costs are staggering. The Ponemon Institute found that in 2013 each lost data record cost companies an average of $145 per record. A major retailer with millions of leaked credit cards could face more than $100 million in direct costs, including fines, and a university that leaked 40,000 records could suffer over $5.4 million in losses.
Ponemon also found that heavily regulated industries such as healthcare, finance, pharmaceuticals and communications had a per record data breach cost ranging from $177 to $359 — placing them well above the mean of $145. Meanwhile, retailers and public sector organizations had a per-record cost of $105 and $100.
Your Client is at Risk
The risk of exposure for your clients’ businesses is high. In our experience, organizations that have requested an assessment of their current security posture find out that they are much more vulnerable than they thought they were because:
- Criminals will not relent: Once a business is targeted, criminals won’t stop. If a business doesn’t have visibility into attacks as they happen, the criminals will succeed.
- Every business is affected: Banks were once the primary targets of cyber criminals; but today these criminals have broadened their targets and move with lightning speed to steal money, intellectual property, customer information and state secrets across all sectors.
- The perimeter has already been breached and the criminals are inside: Recent attacks demonstrate that victims were compromised for months before they discovered it.
- Assuming that a business has already been breached is today’s prudent security posture.
Lack of Security Talent Available
Underscoring these challenges is the fact that finding security talent is a continuing problem. According to a Forrester survey report that was commissioned by IBM, Surviving the Technical Security Skills Crisis, the vast majority, 86 percent, of security leaders believe that concerns relating to managing information risk were directly related to staffing difficulties. Additionally, an alarming 80 percent of security leaders believe that it is difficult or very difficult to find and hire technical security staff that fit all of their requirements. Without the properly skilled technical staff, chief information security officers (CISOs) are forced to ignore innovation projects and business priorities; instead allocating scarce resources to keep up with basic operational tasks.
Protecting Your Clients
So how do your help your clients protect themselves in this hostile, high-risk environment?
IBM has a full suite of managed security services, and is the trusted security advisor to thousands of the world's leading businesses and governments. This managed service approach to security integrates a broad range of security services with preemptive protection solutions for your entire IT infrastructure, including gateways, networks, and servers.
As an IBM Business Partner, you will be providing your clients with leading managed security solutions that are recognized in a leadership position by the major research analysts, Forrester, Gartner and IDC.
The (cyber) storm is coming. Are you ready to help protect your clients? Email me at dcromwel@us.ibm.com, connect with me on LinkedIn, or follow me on Twitter to talk about joining the IBM Global Technology Services Business Partner team.
Denyse Cromwell-Mackey, Vice President, US Global Technology Services, Business Partner Channel, IBM, is the executive responsible for recruitment and driving sales exclusively through North America Business Partners for the IBM services portfolio of cloud and managed services. Prior to this, Denyse was Vice President North America General Business, Business Partner Channels, IBM and Director of Global Software Group, Business Partner Channels, IBM. CRN magazine named her one of the most powerful 100 women in channels in 2009 and she was relisted in 2014 in recognition of the growth of IBM Services resold through Business Partners.

