Mobile Malvertising on the Rise
Submitted by Craig Campbell on
As the tech market trends show, the use of mobile devices continues to grow, and so do the mobile security threats. And since mobile devices are always on and carried from home, to work, on the weekend outing, to the annual or monthly shopping spree and everywhere else, they’ve become a prime target for ‘malvertising’.
What is Malvertising?
Malvertising (Malicious Advertising) attacks involve the use of online advertising channels to infiltrate malware into the computers of unsuspecting users by embedding malicious code within legitimate advertisements on trusted websites.
How does it work?
Malvertisements are commonly placed on a website in one of these ways:
-
Direct Purchase: At first, a criminal may place a series of malware-free advertisements on a trusted site that runs third-party ads, and leave them alone for several months in order to establish a good reputation. Later on, the criminal will inject a malicious payload into the ad, infecting as many computers as possible in a short amount of time, before removing the malicious code or discontinuing the ad.
-
Ad Exchanges: Attackers position their malicious ad within an ad network or exchange that automatically distributes ad space on websites. This automated ad distribution process through a complex network of exchanges makes it incredibly difficult to track down the original source of the ad, as well as to determine on which sites the ad was published.
-
Exploit Technical Vulnerabilities: Attackers leverage vulnerabilities in the ad servers or other infrastructures to compromise ad networks, DSPs, etc., and through this compromise, they replace legitimate ads with malicious ads, which are then sent out to any number of destinations.
In the recent past, sites that host adult content were known as the main vector of infection for mobile devices, but the new primary vector of mobile infection emerging in 2013 was ‘malvertising’ distributed via Web Ads. The key factor contributing to malvertising outpacing adult content sites as the newest way to infect one’s mobile device is simply traffic, as it should come as no surprise that mobile advertising targets a far broader audience than does porn.
In February 2014, web ads represented the single biggest threat vector for mobile users. [Tweet this]
Moreover, every one in five times a person that went online from their smartphone was redirected to a malware site because of a malicious mobile ad, according to a March 2014 report released by Blue Coat, which discovered a threefold jump from two years ago. That is almost triple the rate in November 2012.
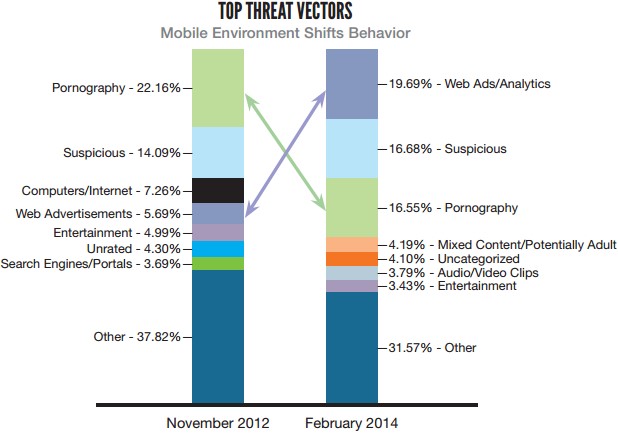
Source: BlueCoat Mobile Malware Report, March 2014
So what’s the reason behind this shift? Like with PCs decades ago, there simply isn’t the awareness among mobile users that something that pops up during browsing or while they’re playing their favorite mobile game could potentially lead to trouble. And this makes malvertising the perfect vector for malicious content.
4 Best Practices:
-
Having an E-App store will provide your enterprise with more options for enabling mobility in BYOD environments and the extended enterprise, without compromising user privacy or company security. All this while still providing your employees with the resources they need to get their jobs done in today’s mobile environment.
-
Provide Secure Web Browser to ensure a secure browsing experience by providing different settings to fit the unique needs of your company and customers. Administrators can define security settings for each ownership type, and real-time adjustments can be made as your needs evolve.
-
Enterprises that have ‘bring your own device’ or corporate mobility initiatives should look at pre-approving mobile apps that present a lower risk of data leakage or privacy violations.
-
And above all, have installed a mobile AntiVirus software such as Bitdefender Mobile Security that is able to provide your employees with ‘full’ protection from mistakenly allowing malware to be installed on their devices, and also proactive protection by warning of websites that could potentially contain some form of malware, or notifying when an Application could be improperly monitoring their activities, or access their personal and possibly corporate information.

